Head of Public Sector at Exponential-e, David Lozdan, speaks to City AM about the investments in data-driven digital healthcare and how this is effectively improving patient outcomes through the National Pathology Imaging Co-operative (NPIC).
Amy Springford, Director of Client Relations at Exponential-e, speaks to SheCanCode, discussing the importance of inclusivity in the workplace and how this would support retaining female workers, as well as implementing flexible working policies for women to juggle their work-life balance.
Afshin Attari, Director of Public Sector and Unified Platforms, writes for 'Government Transformation Magazine' discussing the four core technologies which could transform the Public Sector.
Our Chief Innovation Officer, Jonathan Bridges, writes for 'Security Boulevard' about the importance of understanding and preparing for ransomware attacks as an IT professional, and the steps you should take to mitigate risks for your business.
On the 18th March 2024, the Information Commissioner's Office issued its updated guidance around the issuing of fines when organisations have been found liable for the integrity of their customers' or end users' data being compromised. It is already well-established now that failure to ensure critical data remains secure will result in costly fines, as we have seen repeatedly in multiple high-profile cases over the years.
In October 2023, the British Library suffered "one of the worst cyber incidents in British history," as described by Ciaran Martin, ex-CEO of the National Cyber Security Centre (NCSC).
The notorious Rhysida ransomware gang broke into one of the world's greatest research libraries, encrypting or destroying much of its data, and exfiltrating 600 GB of files, including personal information of British Library staff and users.
Any organisation that has tried to recover from a ransomware attack knows that it can be time-consuming and costly. Companies hit by an attack must choose between paying a ransom or recovering encrypted data from a backup.
Unfortunately, ransomware gangs are too aware that they can leverage significantly higher ransoms from their corporate victims if they have also compromise the company's backups. For this reason, we are seeing more and more cyber attacks targeting backups because they know that organisations desperately need them to recover if they want to avoid paying a ransom to cybercriminals.
Although the sector as a whole has traditionally been comparatively wary of the ever-increasing pace of technology, legal services are increasingly data driven, with an abundance of AI-related discussion emerging within legal technology circles. The core Document Management Systems (DMS) and Practice Management Systems (PMS) remain the centre of focus for how and where to deploy a variety of rapidly maturing SaaS platforms, or dedicated, highly customised suites.
Now more than ever, effective collaboration and communication are the keys to success. Throughout 2020, we saw a widespread shift in how we interact with each other, both in and out of work, and how we stay connected to our colleagues and customers. Just consider the following:
The digital landscape is evolving at a rate that's never been seen before and is set to continue accelerating in the years ahead. In such a fast-paced environment, the ability to work flexibly, responding to unexpected challenges and optimising the time-to-market for new innovations, is critically important for all organisations - whether they're ambitious start-ups or established global leaders. While IT infrastructure must certainly support this - hence the widespread phasing out of legacy infrastructure in favour of increasingly sophisticated Cloud transformation strategies - any new technology will be of limited effectiveness if processes and methodologies do not evolve in parallel.
After several years of serious global upheaval, it is clear that resilience, agility, and the ability to adapt to the unexpected are critical priorities for all organisations – regardless of size or sector. However, this accelerated pace of change has, in many cases, revealed the limitations of existing IT services. With an increasing emphasis on on-demand services and a highly fluid workforce, legacy services and their systems often struggle to support new propositions and customers' evolving needs, which will – in turn – make maintaining a competitive advantage difficult, if not near impossible.
We're all trying to do more with less, whether that's making our monthly shop go further and reducing our utilities consumption at home or doing more with our organisations' available budgets and resources in our professional lives. But while getting the most out of the resources we have available is certainly admirable and sensible, our most precious resource – one that we cannot replenish once it's been used – is all-too-frequently neglected: our time.
From day-to-day consumer banking to high-profile asset and wealth management, the way we all access financial services is changing in ways that would have been inconceivable just a few years ago. Online banking is now firmly established, allowing customers to manage their money securely within a few clicks - anytime, anywhere and without the need to visit a branch. A 2022 survey revealed that the quality of the online experience was a key factor in 81% of adults' choice of bank1.
"When it comes to digital transformation, the personal touch is often what takes projects from 'good' to 'exceptional'. Plenty of companies can deliver technology, but it's the relationships that really drive innovation in long term."
Philip Button, Regional Business Manager – Enterprise
As a long-standing technology partner for multiple financial organisations across the UK, the team at Exponential-e have been observing the sector's evolving relationship with technology for some time - both the growing demand for a higher standard of operational resilience, and an increasing awareness of the challenges and opportunities that Cloud transformation presents.
The Finance sector has always been one of the most dynamic, rapidly evolving industries, and this shows no signs of changing any time soon. But while shifts in the landscape may well open new opportunities, they will also come with new challenges, and it is the organisations who are ready and able to face these head-on who will continue to thrive in the years ahead.
Working from home can at times be compared to Marmite - you either love it or hate it. You have people that regularly work from home and find themselves far more efficient and productive doing so, and then you have people that are generally office-based and fear the loss of the structure of the day and the social interaction.
With the majority of office workers now being asked to work from home, we've spoken to some of our regular home workers to get their 10 top tips for working from home, and how to get the most out of it and still feel connected to the wider team.
1. Do have a good working environment
Sitting up in bed or on the sofa sounds nice, but your back won't thank you as the day goes on. You should try to create a suitable working environment where you can sit up properly and have your laptop at the correct working height. Whether it's sat at the kitchen table or in your study, try and create an area clear of clutter. Why not try re-arranging some of your house plants to make your 'office' more inviting?
3. Do use video, it's good for all parties
Much of communication is non-verbal. Seeing your colleagues, clients or suppliers on video encourages interaction and engagement. But don't forget, everybody else can see you – make sure you're dressed appropriately and you've not just got out of the shower!
4. Do remember you can blur your background when on video calls
Using Microsoft Teams? You can blur your background on video calls, meaning that the pile of your kids' toys in the corner won't be visible. Handy right!? If you're using Zoom, there is a great feature that allows you to create a 'virtual background' – video call while on the moon, anyone?
6. Do schedule in 'virtual coffee breaks'
Why not schedule 20 minutes in the morning and afternoon to have a short social period with your team? You can all jump on a video call while you recharge your batteries with caffeine and talk about anything but work. Being able to keep some of the social side has a lot of benefits for all involved.
8. Do have some background noise if it helps you focus
If you're the sort of person that finds sitting in silence mind-numbingly boring, why not turn on the radio? Keep the volume low so you can still focus on your tasks and not get distracted. Just like in the office, if you find yourself drifting away from work due to the noise, make sure you refocus yourself.
9. Do have a routine
It's easy to slip into a 'lazy' way of working, potentially even be tempted to stay in your dressing gown all day, but it's important to still have a routine and set your mind up for the day. Try to keep the routine you had when going into the office - wake up, shower, have breakfast - you'll feel far more ready to tackle the day ahead.
And finally, the one that many people dread…
10. Don't worry about the kids/pets coming into the room
Cat jumped up on your keyboard? Your kid asking if they can have some crisps? We're all human and these things happen. Embrace them if they happen to you, and help others feel comfortable when it happens to them - everybody understands the situation that we find ourselves in. We'll all have stories to tell about 'those' moments in the coming weeks!
Now, most of these points will be stating the obvious for those of us that work from home on a regular basis. The challenges that we will all face in the coming weeks are some of the common challenges faced by regular home workers. Once this all dies down, and we are all able to return to the office environment, why not reach out to your colleagues that work from home to make sure they feel part of the team?
With the current global situation, the past week has shown the importance of being able to create the Digital Workspace to provide flexible working solutions for your workforce.
I decided to write a blog around how Microsoft's Teams, a Unified Communication as a Service (UCaaS) solution, has enabled my productivity to not slip despite the whole of my team now having to work from home thanks to Coronavirus.
Twitter, WhatsApp and other means of consumer service technology are becoming part and parcel of communicating at work alongside Unified Communications (UC) technologies. As a result, the boundaries between our work and personal lives are becoming increasingly blurred.
Ransomware is malware that encrypts an individual's files so that they no longer have access to them, and subsequently demand payment for the files to be released. Usually the payment is asked to be made in an untraceable cryptocurrency form, such as Bitcoin. The most common way ransomware ends up on an individual's computers is through email spam, which individuals will click on and open.
Unfortunately, the files cannot be decrypted without a mathematical key which is only known by the cyber attacker, and the reason why many individuals tend to pay up. However, many find that despite paying the ransom, their files remain encrypted.
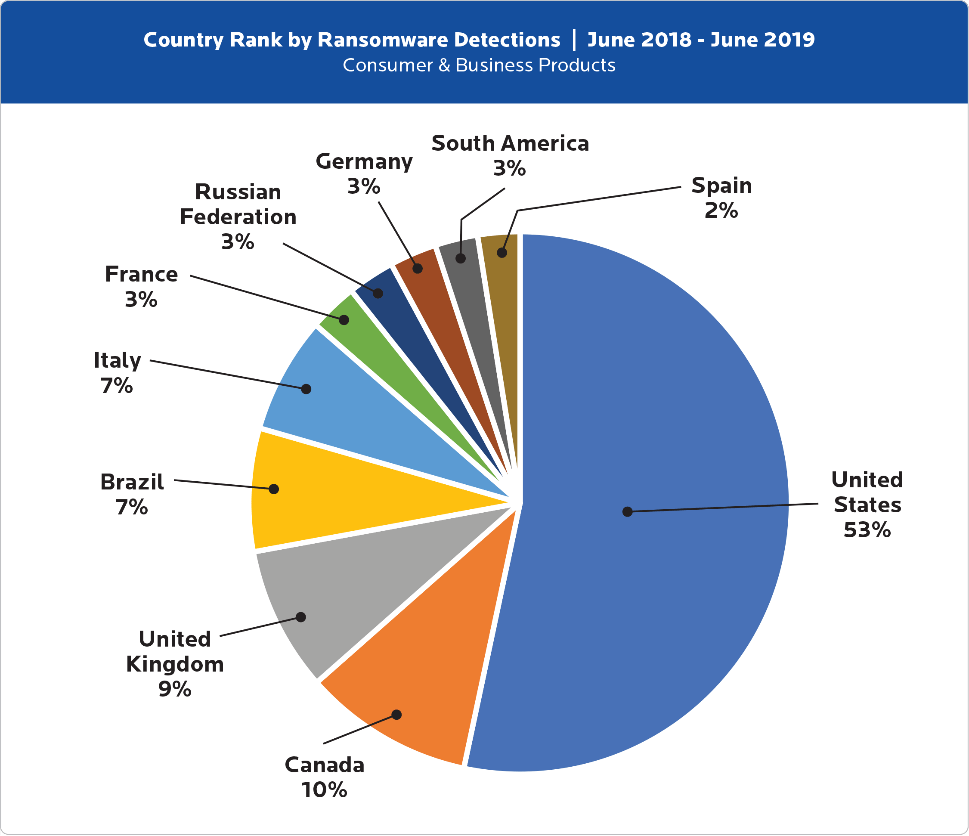
When looking at which countries were affected by ransomware attacks the most, the UK was found to have the highest percentage out of Europe:
Figure 1: Cybercrime Tactics and Techniques: Ransomware Retrospective Report, Malwarebytes
Despite the NHS facing one of the worst ransomware attacks in May 2017 - the WannaCry ransomware attack - which cost the NHS £92m and caused more than 19,000 appointments to be cancelled (The Department of Health), this chart clearly highlights how organisations in the UK still need to invest more into their Cyber Security solutions to stay protected from ransomware attacks.
At Exponential-e, we help organisations that have been affected by ransomware attacks. Our Head of Cyber Consultancy, Mark Belgrove, discusses a real-life cyber attack in the video below, and shares how Exponential-ehelped mediate the situation.