Mobile App Pen Testing
Secure your applications with professional penetration testing
Protect user data, prevent breaches, and build trust with comprehensive security assessments.
Protect from cyber threats
Uncover and Remediate Vulnerabilities
Before Attackers Exploit Them
In today's mobile-first world, your applications are the gateway to your business. But this means your customers and end users expect complete peace of mind that their data will always remain secure as they access your services. Mobile app security vulnerabilities can expose sensitive data, compromise user trust, and damage your brand reputation.
Exponential-e's Mobile Application Penetration Testing service helps you uncover and remediate these vulnerabilities before attackers are able to exploit them. We employ a comprehensive, holistic approach, analysing your app from code to network traffic, ensuring no stone is left unturned.





Why pen test your mobile apps?
Web Application Penetration Testing (VAPT) - Our expert team conducts rigorous assessments to uncover vulnerabilities in your web applications, simulating real-world attacks.
Stay ahead of the latest cyber threats - Bad actors continually identify and exploit new attack vectors in order to compromise corporate infrastructure, but a proactive approach to application testing provides the all-important edge against the latest threats.
Features

API Security
Ensure secure communication between your app and backend services with API penetration testing.

Static Application Security Testing (SAST)
Analyse your app's source code for vulnerabilities without requiring execution.

Dynamic Application Security Testing (DAST)
Simulate real-world attacks to find vulnerabilities while the app is running.

Code Inspection
Deep dive into your app's code to uncover hidden flaws and misconfigurations.

Application Assessment
Test your app on real devices to identify vulnerabilities in its functionality and data handling.

Traffic Inspection
Monitor and analyse network traffic to ensure secure communication protocols are used.

Mobile Device Management Assessment
Evaluate the security of your MDM solution for additional protection.

Vulnerability Identification and Testing
Go beyond automated scans with manual testing to find critical vulnerabilities and eliminate false positives.

Risk Assessment and Recommendations
Prioritise identified vulnerabilities and provide actionable steps for remediation.

Immediate Reporting of High-risk Issues
Get notified instantly of critical vulnerabilities that could be exploited by attackers.
Why Choose Exponential-e?
Schedule a free consultation to discuss your mobile app security needs.
Comprehensive Approach - We cover all aspects of your mobile apps’ security - from code to infrastructure.
Expert Team - Our team of skilled pen testers has extensive experience in mobile app security.
Actionable insights - We provide detailed reports and recommendations for effective remediation.
Peace of Mind - Gain confidence knowing your mobile apps are secure and protected.
Multi-site digital transformation
delivers a fully optimised supply chain and enhanced patient care
We have quite an unusual setup when it comes to our IT infrastructure, but the Exponential-e team have been superb throughout, ensuring everyone stays in the loop and that our goals are consistently achieved. We're looking forward to continuing working with them.
Stuart MacMillian - West Yorkshire Association of Acute Trusts.
Accreditations and Frameworks
Environmental Management
Certificate number: EMS 648194
Quality Management
Certificate number: FS 545046
Business Continuity Management
Certificate number: BCMS 6073420
SOC2 - Type 2 Compliance
A SOC2 - Type2 Compliance is an internal controls report capturing how a company safeguards customer data and how well those controls are operating. These reports are issued by independent third party auditors covering the principles of Security, Availability, Confidentiality, and Privacy.

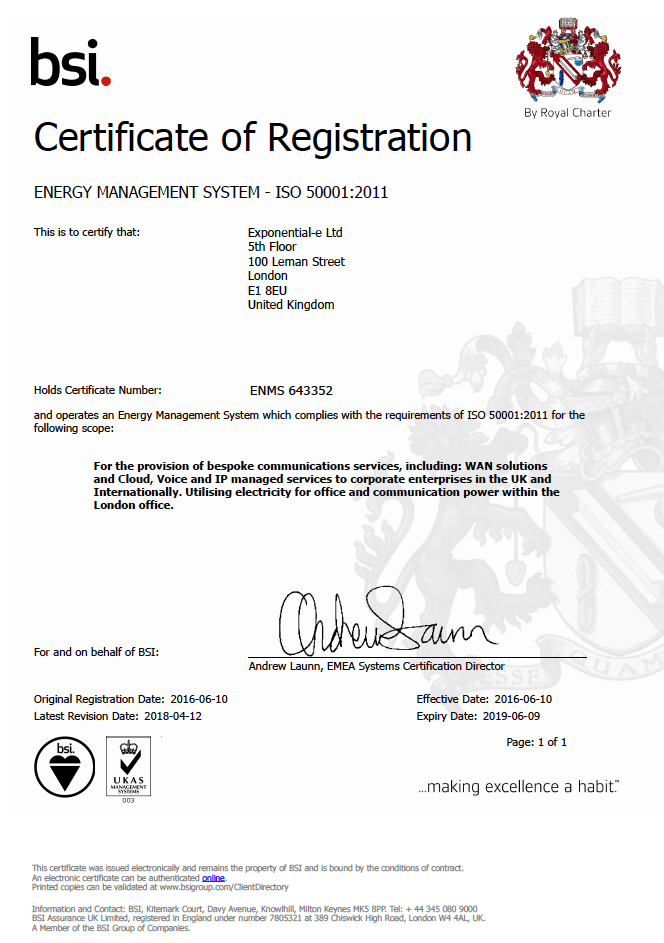
Energy Management
Certificate number: EMS 648194
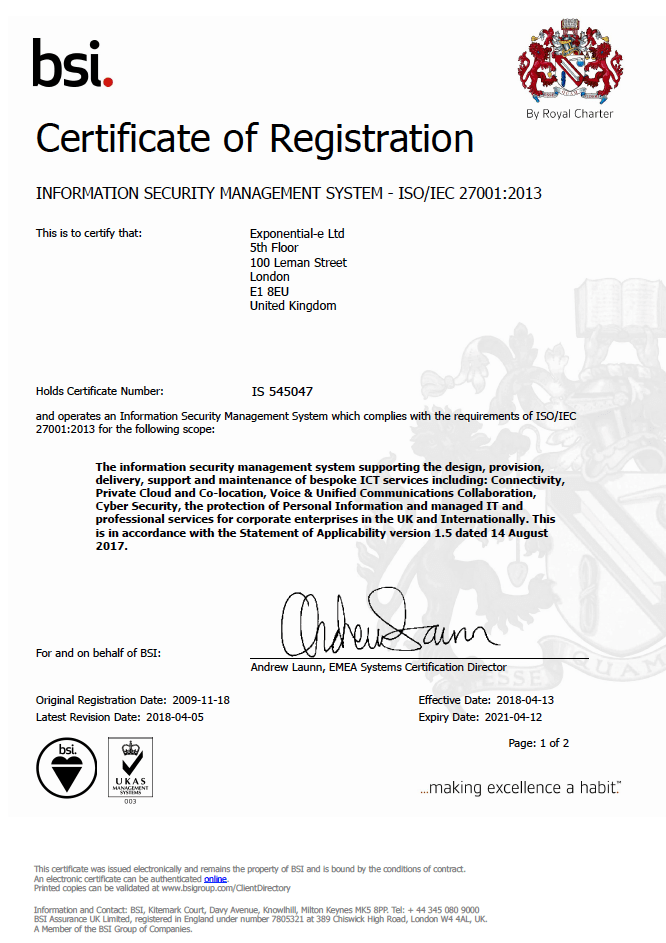
Information Security Management
Certificate number: IS 545047
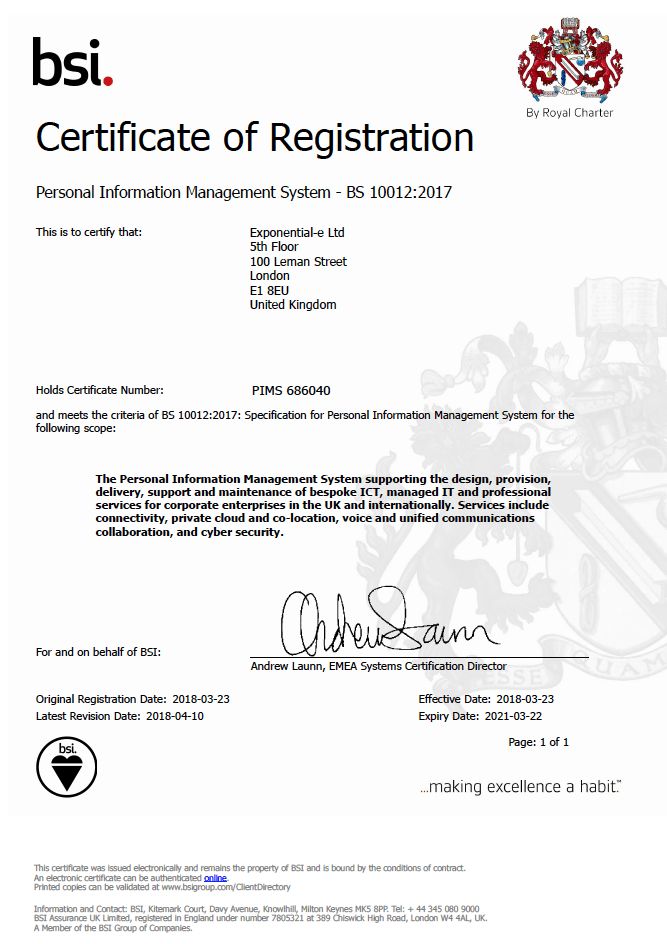
2017 Data Protection
Certificate number: PIMS 686040
Cloud Security
Certificate number: STAR 6073412
Service Management
Certificate number: ITMS 562540
ISO 27001
Certificate number: IS545047
PCI DSS
The PCI DSS is a set of comprehensive requirements for enhancing Network security. It is a multifaceted security standard that includes requirements for: Security management, policies and procedures, network architecture and their critical protective measures. This comprehensive standard is intended to help organisations proactively protect its Network.

The CCA Global Standard
The CCA Global Standard is a globally-recognised accreditation that acknowledges excellence in organisations’ customer service strategies, in order to develop a high standard of customer experience across all sectors, all over the world. The assessment process looks closely at a number of areas, including managing the transition to new working models, agent wellbeing, monitoring and analytics, and the overall customer journey.

ISO 27001
Certificate: IS545047
SOC2 - Type 2 Compliance
A SOC2 - Type2 Compliance is an internal controls report capturing how a company safeguards customer data and how well those controls are operating. These reports are issued by independent third party auditors covering the principles of Security, Availability, Confidentiality, and Privacy.

The CCA Global Standard
The CCA Global Standard is a globally-recognised accreditation that acknowledges excellence in organisations’ customer service strategies, in order to develop a high standard of customer experience across all sectors, all over the world. The assessment process looks closely at a number of areas, including managing the transition to new working models, agent wellbeing, monitoring and analytics, and the overall customer journey.

PCI DSS
The PCI DSS is a set of comprehensive requirements for enhancing Network security. It is a multifaceted security standard that includes requirements for: Security management, policies and procedures, network architecture and their critical protective measures. This comprehensive standard is intended to help organisations proactively protect its Network.

Applying our customer-first philosophy to the contact centre
Rolling 3 month average. Industry average: 17
Our commitment to delivering excellence
The world’s first real-time NPS - part of our longstanding customer service promise.
Through our own customer service platform, our customers are able to give us feedback quickly and easily, with a click of a button. Our Customer Support teams are immediately notified of feedback so they can respond instantly, in order to quickly closing the loop on any feedback that is less than excellent.
RESOURCES
More Insights
FAQs
Mobile app penetration testing is a simulated attack on your mobile app to identify vulnerabilities that could be exploited by real attackers. It tests the security of your app's code, functionality, data handling, and communication with external systems.
We use a combination of automated tools and manual testing to ensure thorough coverage. This includes static application security testing (SAST), dynamic application security testing (DAST), code inspection, application assessment, traffic inspection, and manual vulnerability exploitation.

GET IN TOUCH
Schedule a free consultation to discuss your mobile app security needs.
Contact Sales: 0845 470 4001
Service & Support: 0800 130 3365
London Head Office
Manchester Office
*Calls to 0845 numbers will cost 7p p/m plus your phone company’s access charge.
All inbound and outbound calls may be recorded for training or quality purposes.