A Step-by-Step Guide to Ransomware Remediation
Demystifying the recovery process post cyber attack
CYBERSECURITY LANDSCAPE
Ransomware remains a lingering threat to organisations across the public and private sectors, from startups to industry leaders - with 66% of organisations experiencing an attack in 2023 alone.
It is therefore essential that your cyber security strategy not only utilises the latest solutions and threat intelligence to secure against attacks, but incorporates a robust remediation process, ensuring you are able to recover and resume trading as quickly as possible in the event of a successful attack, minimising the potential reputational and financial consequences.




The key to Successful Remediation
Falling victim to a security breach can be overwhelming, but understanding the recovery process can bring much-needed clarity and help you take proactive steps to getting operational again as quickly as possible. Due to the diverse nature of corporate infrastructure and the growing range of ransomware attacks utilised by bad actors, the process will vary every time, but the following steps are the key areas that a successful remediation will always incorporate, and form the core of Exponential-e’s own approach to disaster recovery.
The six pillars of effective ransomware recovery

Initial steps
Time is of the essence! Upon receiving your call, our experts initiate immediate containment measures. We begin by isolating the infected device or network to prevent further encryption and lateral spread of the malware. Our team then meticulously gathers information about the attack, including infected files, ransom demands, and any available intelligence on the ransomware strain.

Threat Identification and Eradication
The next step is in-depth forensic analysis. This involves:
- Examining system logs and network traffic for suspicious activity.
- Identifying the specific ransomware variant based on technical markers.
- Determining the attack vector - how the malware gained access.
With the culprit identified, we deploy specialist tools and techniques to neutralise the threat. This may involve:
- Terminating malicious processes and disabling associated scripts.
- Executing rigorous malware removal across all infected systems.
- Employing advanced anti-malware software for comprehensive system cleansing.

Data Decryption
The encrypted files hold the key to your precious data, which means they must be recovered and secured. We leverage:
- Decryption keys - If available, we acquire decryption keys through various means, including collaboration with security researchers or negotiations with responsible disclosure platforms.
- Decryption tools - We utilise advanced decryption tools, tailored to specific ransomware variants.
Throughout this process, we prioritise data integrity, ensuring recovered files remain unaltered and functional.
System Restoration
With the threat neutralised and data recovered, we turn to restoring your systems to full functionality as soon as possible, allowing you to resume trading with minimal disruption. This involves:
- Rebuilding compromised systems, potentially involving secure data wiping and clean installs.
- Updating software and patching vulnerabilities that may have exploited.
- Implementing robust security measures to prevent future intrusions.

Vulnerability Assessment and Patching
Effective remediation extends beyond an immediate recovery, focusing on the long-term protection of corporate infrastructure and the optimisation of the entire security ecosystem. To this end, our cyber security experts:
- Conduct comprehensive vulnerability assessments to identify and prioritise remaining weaknesses.
- Provide actionable recommendations for patching vulnerabilities, updating policies, and strengthening your overall security programme.

Incident Response Training
To minimise the chances of future breaches occurring, and help cultivate a true cyber security culture across all levels of your organisation, we deliver hands-on incident response training, providing your teams with:
- The ability to identify and contain the early warning signs of ransomware.
- Best practice around reporting suspicious activity before it leads to a cyber attack.
- The confidence to handle security incidents calmly and effectively, in line with corporate security policies.
A trusted partner throughout your ransomware mitigation journey
Throughout this journey, we maintain constant communication, keeping you informed about progress, potential challenges, and estimated recovery time. Our goal is to ensure you feel supported and empowered every step of the way, and that you finish the process with the systems, processes, and knowledge needed to secure against future threats.
Ransomware remediation is a complex process, and every attack presents unique challenges. However, with our proven expertise, advanced tools, and unwavering commitment to raising standards of cyber security across the public and private sectors, we are ready to ensure you can resume operations as quickly as possible, and - equally importantly - demonstrate your commitment to maintaining the integrity of your customers’ and end users’ critical data.
Infrastructure, Cloud architecture and solution delivery, drawing on long experience in corporate cyber services, supported by our 24/7 CSOC.
Security-cleared staff, LIST-X accreditation and track record in delivering Defence and Critical National Infrastructure solutions.
Security-cleared staff and track record in delivering ‘Information Assured’ solutions into the Intelligence and CNI sectors.
Multi-site digital transformation
delivers a fully optimised supply chain and enhanced patient care
We have quite an unusual setup when it comes to our IT infrastructure, but the Exponential-e team have been superb throughout, ensuring everyone stays in the loop and that our goals are consistently achieved. We're looking forward to continuing working with them.
Stuart MacMillian - West Yorkshire Association of Acute Trusts.
Accreditations and Frameworks
Environmental Management
Certificate number: EMS 648194
Quality Management
Certificate number: FS 545046
Business Continuity Management
Certificate number: BCMS 6073420
SOC2 - Type 2 Compliance
A SOC2 - Type2 Compliance is an internal controls report capturing how a company safeguards customer data and how well those controls are operating. These reports are issued by independent third party auditors covering the principles of Security, Availability, Confidentiality, and Privacy.

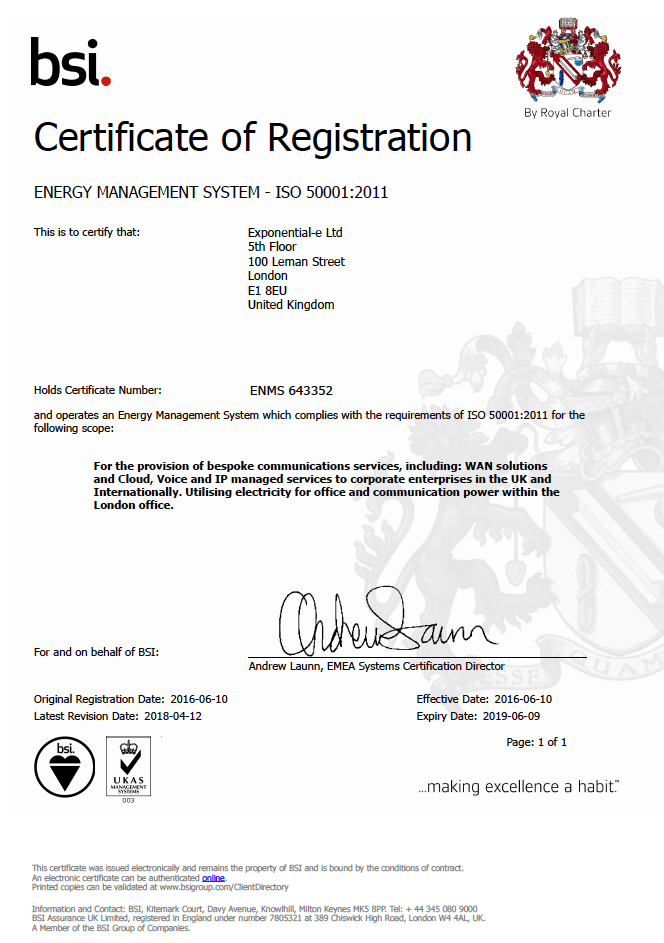
Energy Management
Certificate number: EMS 648194
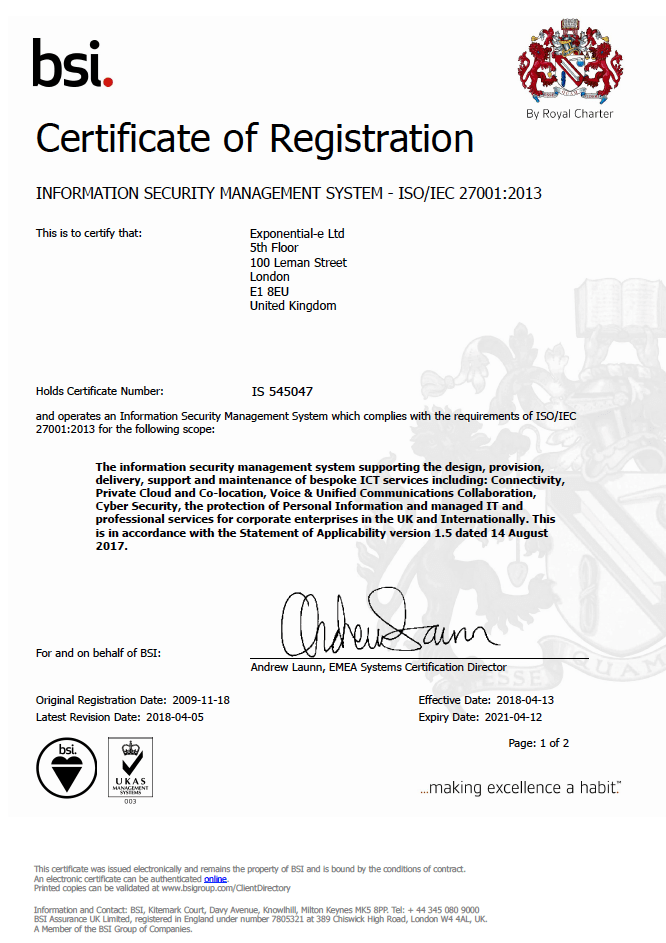
Information Security Management
Certificate number: IS 545047
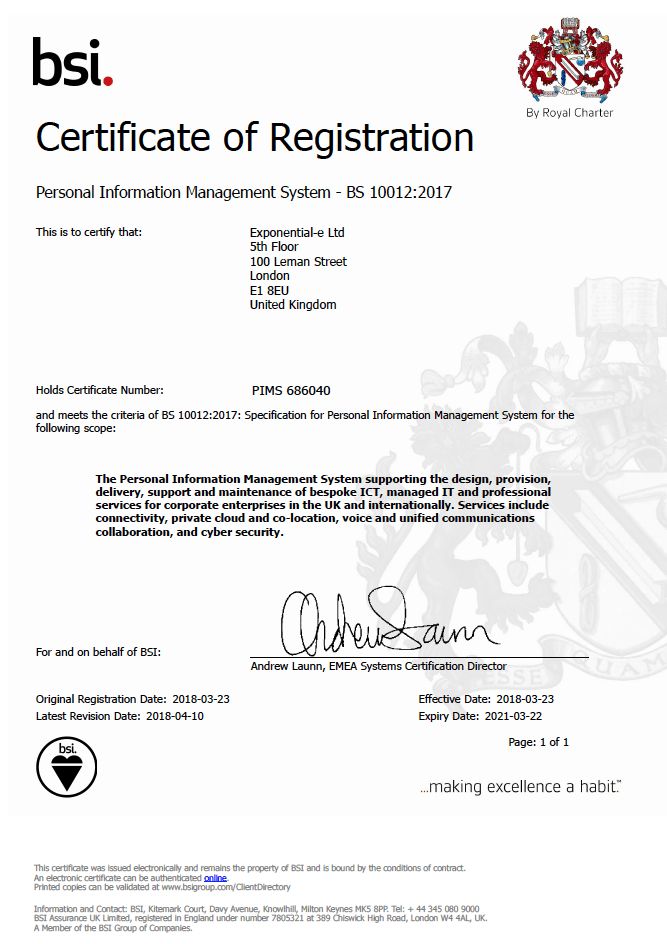
2017 Data Protection
Certificate number: PIMS 686040
Cloud Security
Certificate number: STAR 6073412
Service Management
Certificate number: ITMS 562540
ISO 27001
Certificate number: IS545047
PCI DSS
The PCI DSS is a set of comprehensive requirements for enhancing Network security. It is a multifaceted security standard that includes requirements for: Security management, policies and procedures, network architecture and their critical protective measures. This comprehensive standard is intended to help organisations proactively protect its Network.

The CCA Global Standard
The CCA Global Standard is a globally-recognised accreditation that acknowledges excellence in organisations’ customer service strategies, in order to develop a high standard of customer experience across all sectors, all over the world. The assessment process looks closely at a number of areas, including managing the transition to new working models, agent wellbeing, monitoring and analytics, and the overall customer journey.

ISO 27001
Certificate: IS545047
SOC2 - Type 2 Compliance
A SOC2 - Type2 Compliance is an internal controls report capturing how a company safeguards customer data and how well those controls are operating. These reports are issued by independent third party auditors covering the principles of Security, Availability, Confidentiality, and Privacy.

The CCA Global Standard
The CCA Global Standard is a globally-recognised accreditation that acknowledges excellence in organisations’ customer service strategies, in order to develop a high standard of customer experience across all sectors, all over the world. The assessment process looks closely at a number of areas, including managing the transition to new working models, agent wellbeing, monitoring and analytics, and the overall customer journey.

PCI DSS
The PCI DSS is a set of comprehensive requirements for enhancing Network security. It is a multifaceted security standard that includes requirements for: Security management, policies and procedures, network architecture and their critical protective measures. This comprehensive standard is intended to help organisations proactively protect its Network.

Applying our customer-first philosophy to the contact centre
Rolling 3 month average. Industry average: 17
Our commitment to delivering excellence
The world’s first real-time NPS - part of our longstanding customer service promise.
Through our own customer service platform, our customers are able to give us feedback quickly and easily, with a click of a button. Our Customer Support teams are immediately notified of feedback so they can respond instantly, in order to quickly closing the loop on any feedback that is less than excellent.
RESOURCES
More Insights
FAQs
- Disconnect everything - Immediately isolate all infected devices from your network to prevent further spreading.
- Power down affected systems - If possible, shut down any potentially compromised computers or servers.
- Do not pay the ransom - Paying attackers only funds their operations and doesn't guarantee data recovery.
- Contact us immediately - Our ransomware recovery experts are available 24/7 to guide you through the next steps.
We go beyond simply recovering your data, taking a holistic approach to cyber security and business continuity. Our end-to-end approach encompasses:
- Implementing robust security measures - We fortify your defences with advanced tools and training to prevent future attacks.
- Post-attack vulnerability assessment - We identify and patch any underlying vulnerabilities exploited by the attackers.
- Ongoing security monitoring - We provide continuous monitoring and threat detection to proactively safeguard your systems.

GET IN TOUCH
Are you ready to retake control of your cyber security and IT infrastructure?
If you have experienced a ransomware attack or are keen to take proactive measures to optimise your own remediation process and maintain the leading edge in an evolving threat landscape, do not hesitate to contact us.
Contact Sales: 0845 470 4001
Service & Support: 0800 130 3365
London Head Office
Manchester Office
*Calls to 0845 numbers will cost 7p p/m plus your phone company’s access charge.
All inbound and outbound calls may be recorded for training or quality purposes.