IT Security Assessments
Protect your business with hands-on support from Exponential-e’s own cyber security specialists
Safeguard your critical information and technology assets with expert-led assessments designed to uncover vulnerabilities, prioritise risks, and optimise your IT infrastructure for resilience and growth.
Protect from cyber threats
OUR SERVICES
IT Security Assessment Options
In today's dynamic threat landscape, proactive cyber security measures are not just a good idea, they are a business imperative. Our comprehensive assessments offer the insights and guidance you need to make informed decisions, protect your business, and achieve your strategic objectives.
We offer two forms of IT security assessment, both conducted by our in-house cyber security experts:
Cyber Security Diagnostics:
Understanding Your Security Posture
Cyber Security Diagnostics focuses on identifying your immediate cyber security risks, then providing actionable
advice to strengthen your defences. How it works:

In-depth analysis
Our consultants conduct a thorough evaluation of your IT systems and controls, including on-site assessments and team interviews.

Risk identification
We pinpoint mission-critical assets, assess vulnerabilities, and prioritise the most pressing risks.

Remediation guidance
You'll receive clear recommendations for mitigation actions, enabling swift and effective risk reduction.

Compliance support
Our assessment will support the fulfilment of applicable industry standards and the assessment process for
key accreditations (e.g. Cyber Essentials, ISO 27001).
The result:
Complete IT Infrastructure Assessment:
Optimising Performance, Security, and Resilience
This assessment allows us to design and deliver a comprehensive roadmap for optimising your entire IT infrastructure, enhancing security,
efficiency, and cost savings. How it works:
Thorough evaluation
Our experts meticulously examine all aspects of your IT ecosystem, including hardware, network, Cloud services, business continuity plans, and more.
Vulnerability scanning
Internal and external infrastructure scans pinpoint vulnerabilities in the same way a hacker would, revealing potential risks.
Recommendations and support
We deliver a comprehensive report outlining areas for improvement, along with hands-on support to ensure optimal execution.
The result:
Teamwork & Technology Drive Innovation
with the UK's favourite coffee retailer
When you have a strong tender, but no guarantee the team you're meeting is the team you'll be working with, there's always a concern whether things will work as planned on launch day. But this was never an issue with Exponential-e. All the way through, I had complete confidence in the team we'd be working with.
Barry Firth IT / People Services Programme Manager, Costa.



Accreditations and Frameworks
Environmental Management
Certificate number: EMS 648194
Quality Management
Certificate number: FS 545046
Business Continuity Management
Certificate number: BCMS 6073420
SOC2 - Type 2 Compliance
A SOC2 - Type2 Compliance is an internal controls report capturing how a company safeguards customer data and how well those controls are operating. These reports are issued by independent third party auditors covering the principles of Security, Availability, Confidentiality, and Privacy.

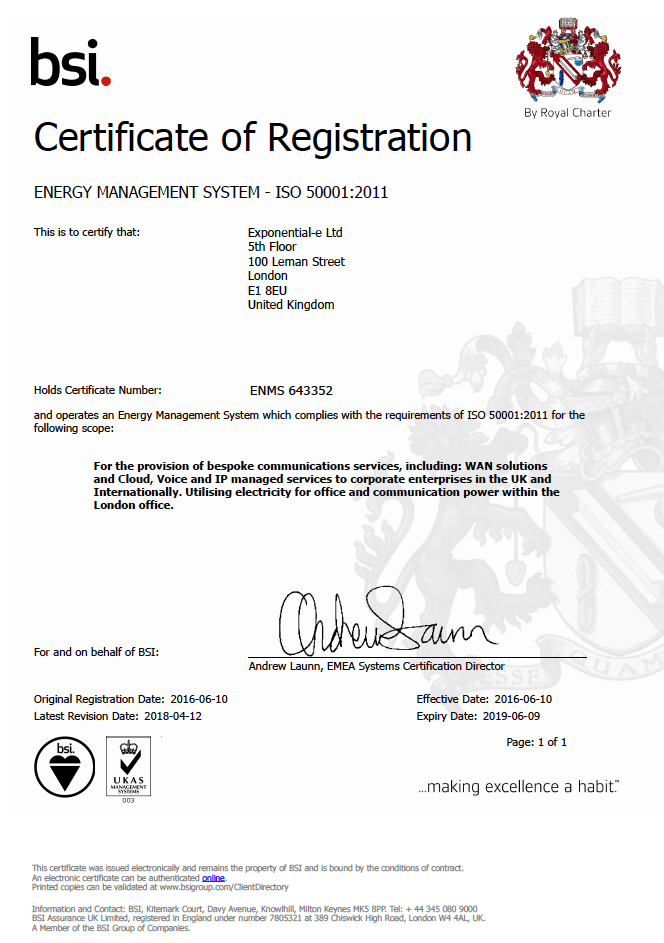
Energy Management
Certificate number: EMS 648194
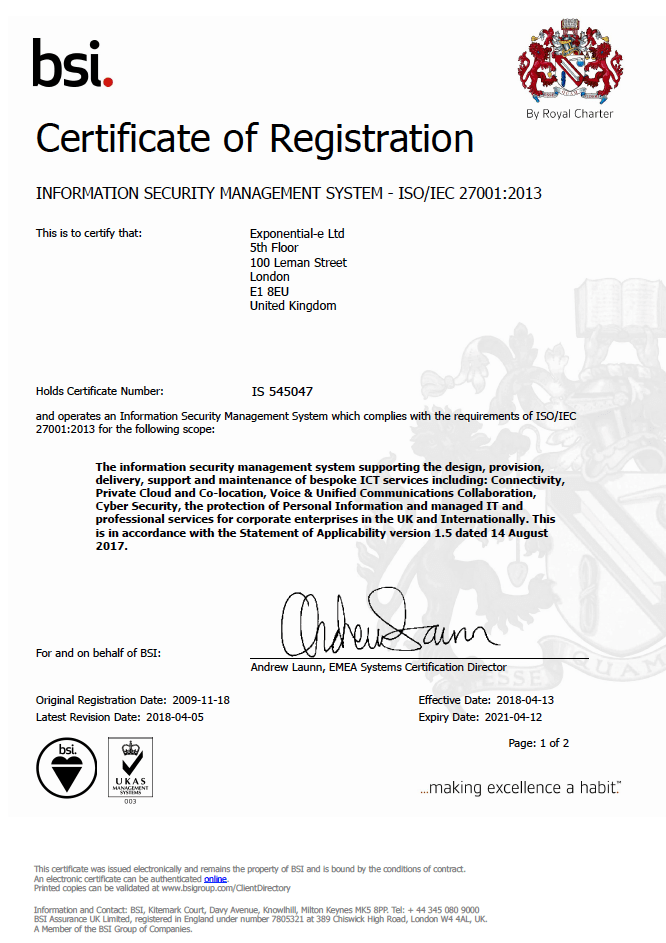
Information Security Management
Certificate number: IS 545047
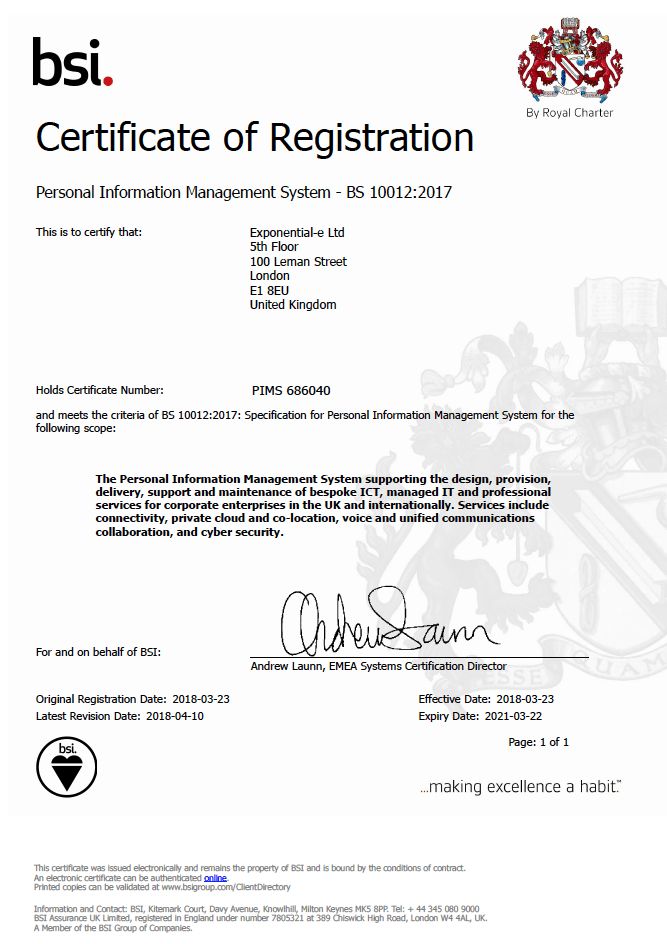
2017 Data Protection
Certificate number: PIMS 686040
Cloud Security
Certificate number: STAR 6073412
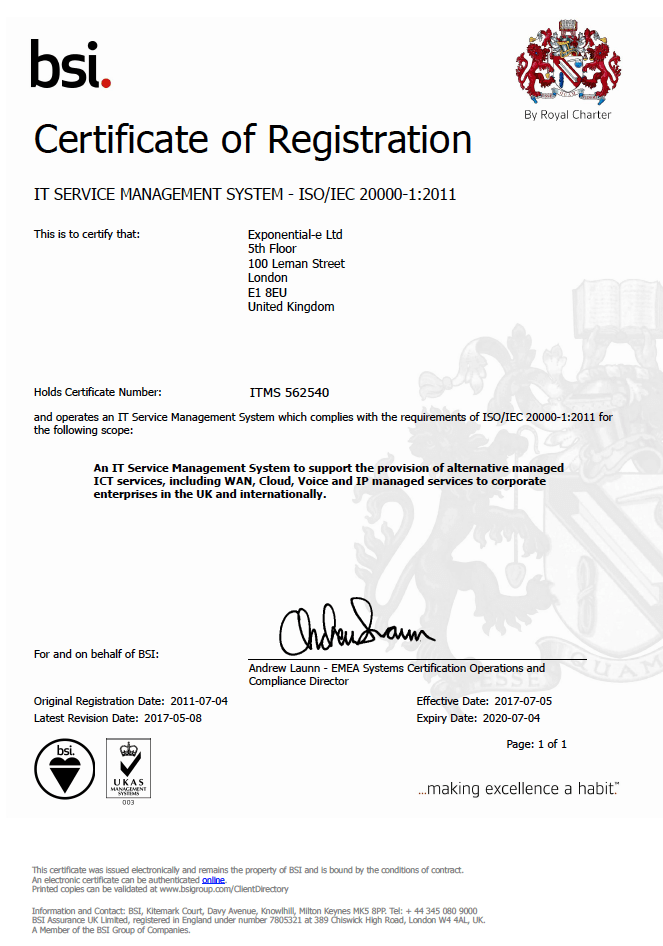
Service Management
Certificate number: ITMS 562540
ISO 27001
Certificate number: IS545047
PCI DSS
The PCI DSS is a set of comprehensive requirements for enhancing Network security. It is a multifaceted security standard that includes requirements for: Security management, policies and procedures, network architecture and their critical protective measures. This comprehensive standard is intended to help organisations proactively protect its Network.

The CCA Global Standard
The CCA Global Standard is a globally-recognised accreditation that acknowledges excellence in organisations’ customer service strategies, in order to develop a high standard of customer experience across all sectors, all over the world. The assessment process looks closely at a number of areas, including managing the transition to new working models, agent wellbeing, monitoring and analytics, and the overall customer journey.

ISO 27001
Certificate: IS545047
SOC2 - Type 2 Compliance
A SOC2 - Type2 Compliance is an internal controls report capturing how a company safeguards customer data and how well those controls are operating. These reports are issued by independent third party auditors covering the principles of Security, Availability, Confidentiality, and Privacy.

The CCA Global Standard
The CCA Global Standard is a globally-recognised accreditation that acknowledges excellence in organisations’ customer service strategies, in order to develop a high standard of customer experience across all sectors, all over the world. The assessment process looks closely at a number of areas, including managing the transition to new working models, agent wellbeing, monitoring and analytics, and the overall customer journey.

PCI DSS
The PCI DSS is a set of comprehensive requirements for enhancing Network security. It is a multifaceted security standard that includes requirements for: Security management, policies and procedures, network architecture and their critical protective measures. This comprehensive standard is intended to help organisations proactively protect its Network.

Applying our customer-first philosophy to the contact centre
Rolling 3 month average. Industry average: 17
Our commitment to delivering excellence
The world’s first real-time NPS - part of our longstanding customer service promise.
Through our own customer service platform, our customers are able to give us feedback quickly and easily, with a click of a button. Our Customer Support teams are immediately notified of feedback so they can respond instantly, in order to quickly closing the loop on any feedback that is less than excellent.
RESOURCES
More Insights
FAQs
Cyber Security Diagnostics is an assessment that focuses on identifying and addressing immediate cyber security risks. It is ideal for businesses that want to quickly assess their current security posture and take proactive steps to protect themselves from cyberattacks.
The Complete IT Infrastructure Assessment is a comprehensive assessment that evaluates every aspect of your IT infrastructure, from hardware and software to network security and business continuity plans. It is ideal for businesses that want to optimise their IT infrastructure for performance, security, and resilience.
There are a number of different ways to test your cyber security posture. The specific methods utilised will depend on the size and complexity of your organisation's IT infrastructure. Some common methods of cyber security testing include:
- Vulnerability scanning - Vulnerability scanners can identify and classify security weaknesses in your IT infrastructure. This can help you prioritise your remediation efforts.
- Penetration testing - Penetration testing is a simulated attack that is designed to exploit identified vulnerabilities and test the effectiveness of your security controls. This can provide you with a more comprehensive assessment of your security posture.
- Social engineering testing - Social engineering testing attempts to trick employees into giving up sensitive information or clicking on malicious links. This can help you identify weaknesses in your organisation's security awareness.
- Red team / blue team exercises - Red team / blue team exercises pit two teams against each other in a simulated attack scenario. This can help you identify and address potential weaknesses in your organisation's incident response plan.

GET IN TOUCH
Are you ready to retake control of your cyber security and IT infrastructure?
Fill out the form to schedule your assessment and start building a more resilient, efficient, and secure digital foundation for your business.
Contact Sales: 0845 470 4001
Service & Support: 0800 130 3365
London Head Office
Manchester Office
*Calls to 0845 numbers will cost 7p p/m plus your phone company’s access charge.
All inbound and outbound calls may be recorded for training or quality purposes.