The security of enterprise networks is a critical priority for all organisations across the public and private sectors, as they are forced to contend with an increasingly turbulent cyber threat landscape. As a result, network teams increasingly find their roles overlap with their organisations' cyber security strategies, with numerous siloed elements now converging.
In light of numerous dramatic shifts in the geopolitical landscape in recent months, this blog has reiterated the need for organisations across all sectors to strengthen and - if necessary - reconsider their cyber security postures, in order to prepare for the anticipated attacks by global bad actors. The legal sector is no exception, particularly as these attacks are anticipated to specifically target the most high-value data.
Although the sector as a whole has traditionally been comparatively wary of the ever-increasing pace of technology, legal services are increasingly data driven, with an abundance of AI-related discussion emerging within legal technology circles. The core Document Management Systems (DMS) and Practice Management Systems (PMS) remain the centre of focus for how and where to deploy a variety of rapidly maturing SaaS platforms, or dedicated, highly customised suites.
Whatever sector you operate in and whatever your long-term business goals, your network is the foundation of your future success. With the distributed workforce now firmly established and customer interactions taking place over an evolving range of channels, business is now truly interconnected, with seamless, secure dataflows its lifeblood.
Secure Access Service Edge (SASE) represents an elegant convergence of network and security technologies as a single, end-to-end solution, perfectly suited to the modern distributed workforce and the increasingly dynamic nature of corporate networks. As a growing number of organisations are discovering, SASE has the potential to completely transform the way we design, deploy, manage, and scale corporate networks. Indeed, 60% of IT leaders are ready to fully embrace SASE by 2025*.
Despite the numerous interconnected elements now involved in effective digital transformation, the network remains the foundation of everything, ensuring any investment in new technologies delivers the best possible ROI, and that teams at all levels are empowered to deliver their very best, 24 / 7. As such, the digital transformation journey must always begin with a full network transformation.
To Test or Not to Test? - When it comes to IT disaster recovery and remediation processes, regular testing is not a 'nice to have' - it's absolutely essential!
This isn't hyperbole on my part. You just have to look at the news on any given day. We've all heard the horror stories of organisations in both the public and private sectors experiencing prolonged downtime during disasters due to inadequate preparation, lack of testing, and the unsuitability of their legacy remediation processes and systems.
On the 18th March 2024, the Information Commissioner's Office issued its updated guidance around the issuing of fines when organisations have been found liable for the integrity of their customers' or end users' data being compromised. It is already well-established now that failure to ensure critical data remains secure will result in costly fines, as we have seen repeatedly in multiple high-profile cases over the years.
In October 2023, the British Library suffered "one of the worst cyber incidents in British history," as described by Ciaran Martin, ex-CEO of the National Cyber Security Centre (NCSC).
The notorious Rhysida ransomware gang broke into one of the world's greatest research libraries, encrypting or destroying much of its data, and exfiltrating 600 GB of files, including personal information of British Library staff and users.
The GDPR deadline day of 25th May has been and gone, but sticking to the legislation remains as important as ever. This is because GDPR is, in fact, not something that can just be 'done'; instead, it is ongoing and needs to be constantly changed and updated. The onus is on housing associations to comply with GDPR not just today, but in six months, a year, two years, and beyond.
In part one of this two part blog series, we looked at why "bricks-and-mortar" retailers are embracing Digital Transformation in order to compete with the new breed of online retail giants.
In part two, we look at the specific challenges Digital Transformation is throwing up for the high street, and how these challenges can be addressed.
After several years of serious global upheaval, it is clear that resilience, agility, and the ability to adapt to the unexpected are critical priorities for all organisations – regardless of size or sector. However, this accelerated pace of change has, in many cases, revealed the limitations of existing IT services. With an increasing emphasis on on-demand services and a highly fluid workforce, legacy services and their systems often struggle to support new propositions and customers' evolving needs, which will – in turn – make maintaining a competitive advantage difficult, if not near impossible.
As the Financial Services (FS) industry continues to adopt and leverage digital technologies to innovate and deliver customer-centric outcomes, there is also a major focus on inward change, on improving employee experience through streamlining, simplifying and consolidating platforms, infrastructure and processes. Of course, Digital Transformation comes with an abundance of risks. Some of these are already widely recognised and covered by the mainstream media, some are newly emerging, and others are as yet unknown.
Ransomware is malware that encrypts an individual's files so that they no longer have access to them, and subsequently demand payment for the files to be released. Usually the payment is asked to be made in an untraceable cryptocurrency form, such as Bitcoin. The most common way ransomware ends up on an individual's computers is through email spam, which individuals will click on and open.
Unfortunately, the files cannot be decrypted without a mathematical key which is only known by the cyber attacker, and the reason why many individuals tend to pay up. However, many find that despite paying the ransom, their files remain encrypted.
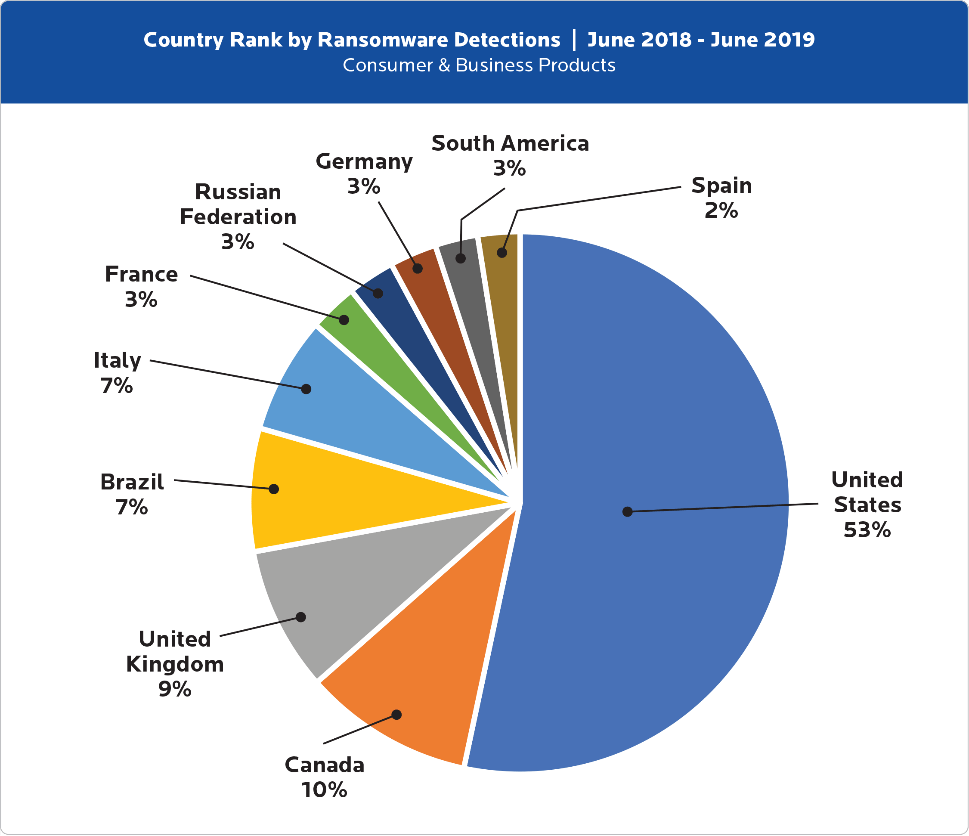
When looking at which countries were affected by ransomware attacks the most, the UK was found to have the highest percentage out of Europe:
Figure 1: Cybercrime Tactics and Techniques: Ransomware Retrospective Report, Malwarebytes
Despite the NHS facing one of the worst ransomware attacks in May 2017 - the WannaCry ransomware attack - which cost the NHS £92m and caused more than 19,000 appointments to be cancelled (The Department of Health), this chart clearly highlights how organisations in the UK still need to invest more into their Cyber Security solutions to stay protected from ransomware attacks.
At Exponential-e, we help organisations that have been affected by ransomware attacks. Our Head of Cyber Consultancy, Mark Belgrove, discusses a real-life cyber attack in the video below, and shares how Exponential-ehelped mediate the situation.
Phishing is the fraudulent use of electronic communications to try and obtain sensitive information, such as usernames, passwords and credit card details by posing as a legitimate institution. Phishing attacks attempt to get individuals to click on a malicious link and enter confidential information to steal their identity, funds or to be the first step in a serious cyberattack against an organisation.
All organisations store data, and regardless of whether it's a recipe or an algorithm, this data is an organisation's most prized asset, which is why hackers make it their target. The Cyber Security Breaches Survey 2019 from the Department for Digital, Culture, Media & Sport (DCMS) found that 32% of businesses identified cyber security breaches or attacks in the last 12 months, which have cost an average of £4,180 in lost data and assets